Denmark is doing the right thing Denmark to tackle deepfakes by giving people copyright to their own features | Deepfake | The Guardian
M&S calls for mandatory ransomware reporting | Computer Weekly
Marks & Spencer chairman Archie Norman has described the recent ransomware attack on the retailer’s systems as something akin to an “out-of-body experience” as he called for cyber attack victims to be brave, bite the bullet, and be open and transparent about their experiences.
Open letters to Third Party Suppliers
It has been a couple of weeks of open letters to suppliers :
Big moves from Microsoft Notepad Microsoft is updating Notepad with text formatting and Markdown support | The Verge
The stolen iPhone market
Inside the Stolen iPhone Market 📲
it is one of the most important nodes in a supply chain for second-hand technology that starts in the west, travels through wholesalers in Hong Kong and on to markets in mainland China and the global south.
Guidelines for secure AI design and development
Guidelines for providers of AI systems, whether custom-built or built on top of external tools and services. NCSC guidelines
Defending Against UNC3944 AKA Scattered Spider
Defending Against UNC3944 AKA Scattered Spider
To counter UNC3944, organizations need robust defenses involving identity verification and advanced authentication methods. Implementing phishing-resistant multi-factor authentication (MFA), minimizing reliance on SMS for authentication, and eliminating publicly available personal data verification are practical steps. Secure the identity verification process with methods like on-camera checks to thwart impersonation attempts.
Training staff to identify and respond to unusual IT requests is crucial. This includes understanding ploys like fake IT calls, email phishing attempts, and odd requests for credential verification, which are characteristic of UNC3944 operations.
A lot of customers will be watching to see what happens with Tata after being linked to another beach - M&S
Researchers Dump 2 Billion Scraped Discord [Messages](Online gizmodo.com/researche…)
Another interesting article about M&S by the FT. This year will sure be a case study for future professionals and students in the industry.



Dragon Force, Scatter Spider and english speaking youngsters behind recent cyber attacks www.bbc.co.uk/news/arti…
Interesting results for M&S, almost £300m taken off 2025 profits and an expectation of July being the earliest when online shopping will continue. I expect this impact to be several years to fully absorb.
It is going to be interesting to see how these ransomware payments are made. Personal data taken in UK legal aid cyber attack | Reuters
They shared evidence proving that they had stolen a huge amount of private customer and employee information
M&S and Co-Op: BBC reporter on talking to the hackers - BBC News
Japan Introduces the Active Cyberdefence Law
The ACD does not permit surveillance of domestic communications, but it allows Tokyo to monitor IP addresses used in communications between foreign countries that pass through Japan, and between Japan and the rest of the world.
This provides a workaround to the constitution’s domestic privacy protections, while addressing the fact that the overwhelming majority of cyber attacks on Japanese entities originate from overseas, according to the government.
M&S comms finally goes out 👏🏽
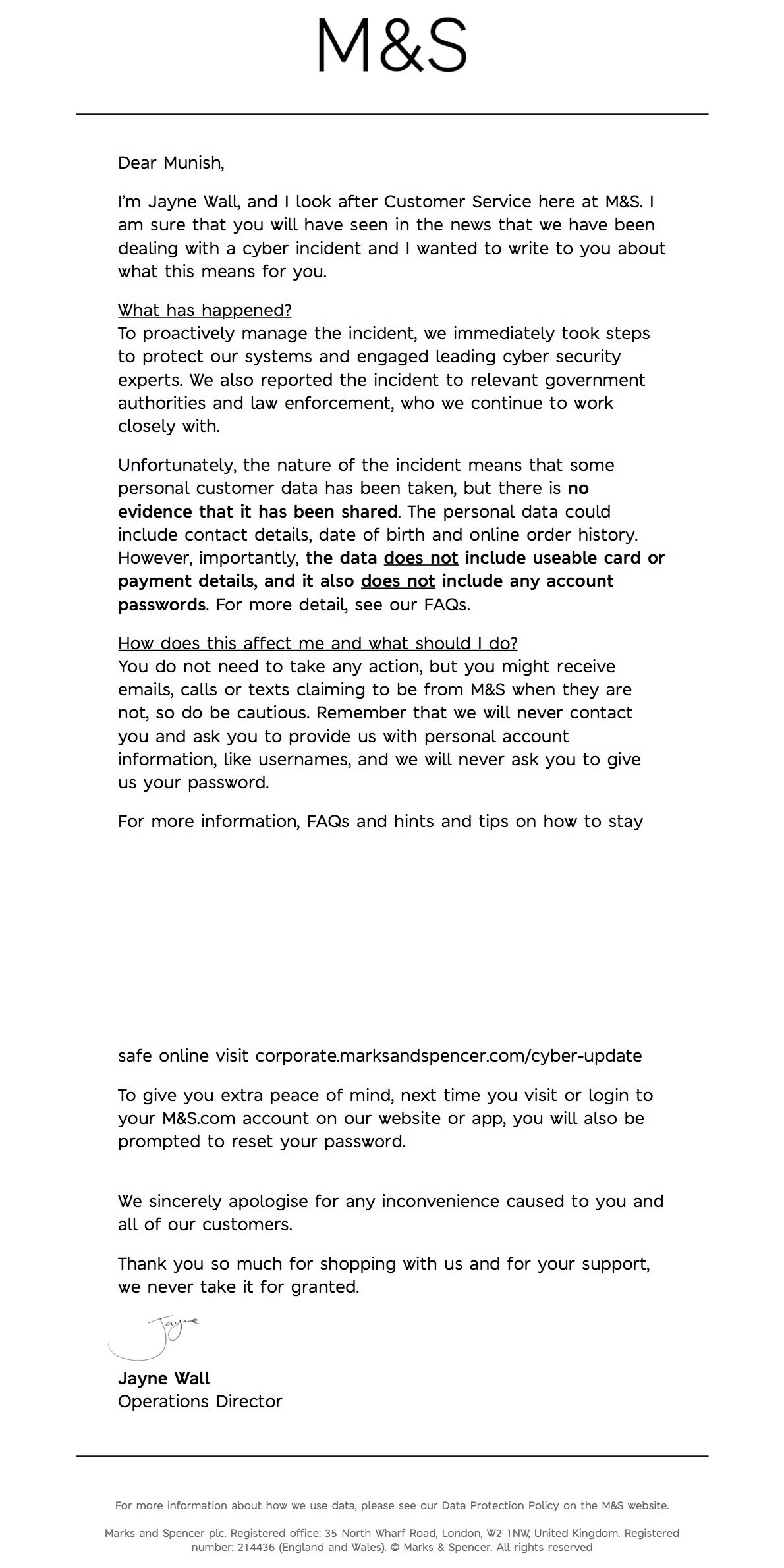
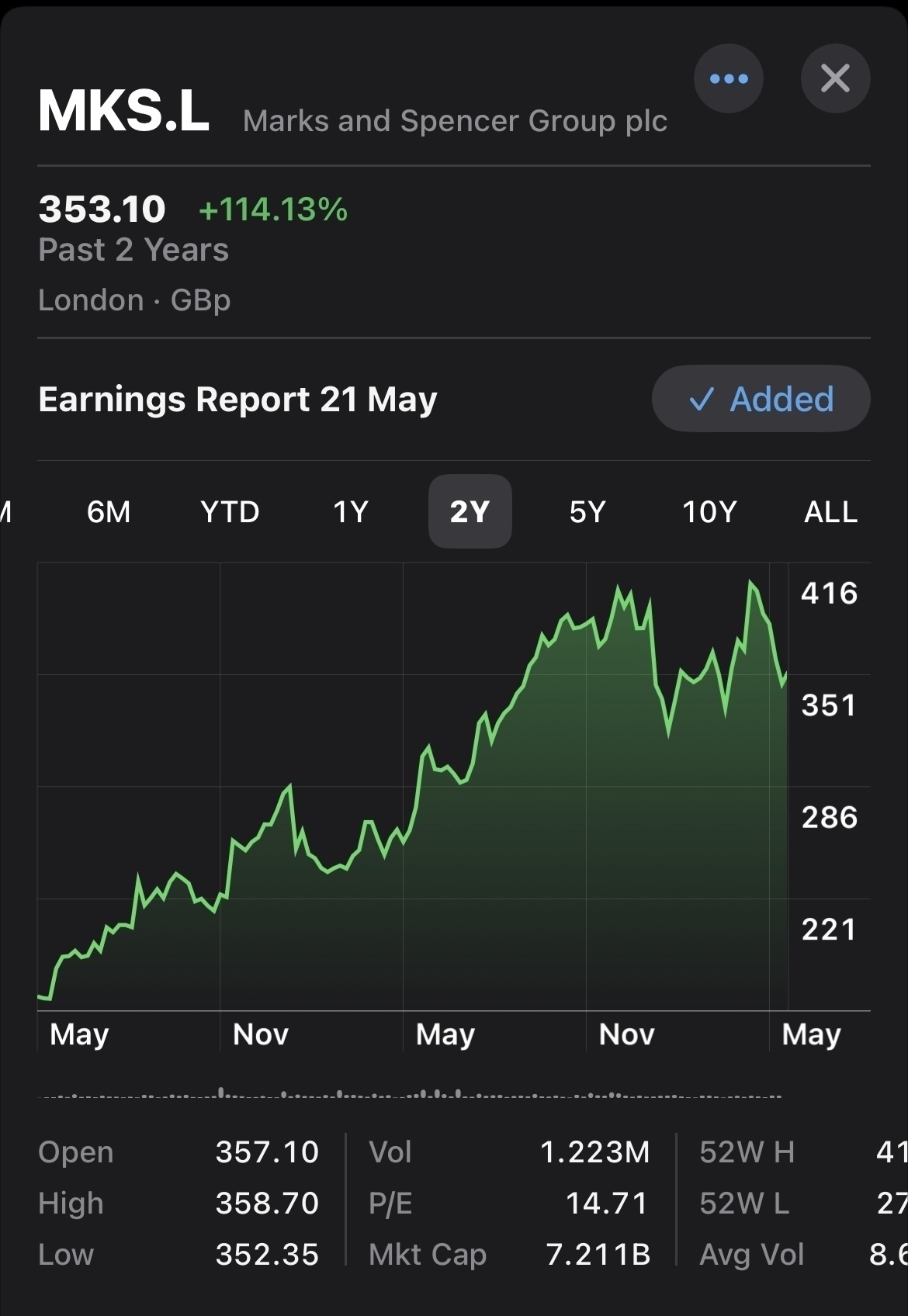
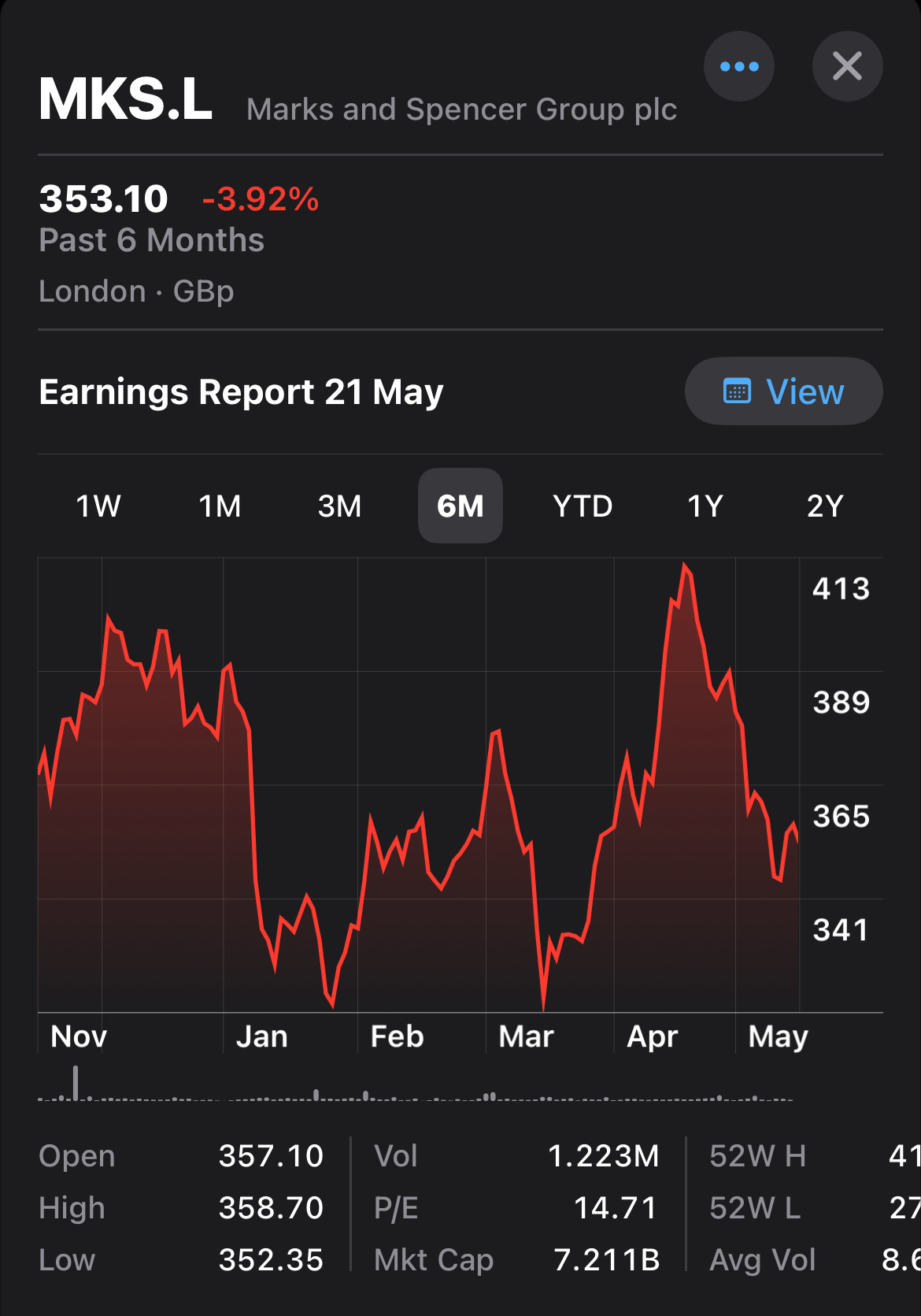
Really surprised that M&S online is still down for purchases. Must be ensuring an overhaul of systems and approach. Stock is not bad over the two years.
A new ecosystem of assured Cyber Resilience Test Facilities will allow vendors to demonstrate the cyber resilience of their products New assurance initiatives to help boost confidence in… - NCSC.GOV.UK
